Who is ????
White Hat,Grey Hat and Black Hat Hackers
 |
| Hacker's Hat |
White Hat Hackers
People who specialized hacking and check the issue/faults in the system.
These people are called Ethical Hackers.
Good guy.
They use their skills legally. { Computer Security Experts, They protects our system from Black Hat Hackers }
Hackers that are authorized.
Grey Hat Hackers
People who exploit the security to the attention of the owner.
These people are called Skilled Hackers.
Combination (mixture) of Black hat and White hat hackers.
Hackers doing good work without any permission.
Black Hat Hackers
People who enters(break) in the network and harm to the network and property of the any owner.
These people are called Crackers.
Bad guy.
They use their skills for illegal purpose. { Hack Bank Accounts, Steal Debit / Credit cards and so many illegal activities }
Hackers that don't have any permissions.
If you have any concerns or any difficulties on this guide then feel free to place a reply on this thread to get instant help.
What is Footprinting
The art of Gathering Information
The purpose of footprinting is to learn as much as possible about a systems, its remote accesss capabilities, its ports and services, and all the aspects of its security.
To successfully hack a system, it is important to know the intricate details,if not everything, about that system.
While footprinting can be used to attack a system,it can also be used to protect it.
Information Gathering invovlves
Finding the target’s URL (Uniform Resource Locator)/ IP address
Footprinting through job sites.
Using Google search for more results.
Finding out the ‘ who is ’ record of the target domain.
BENEFITS OF FOOTPRINTING
Stealth :- The biggest advantage of footprinting is that it’s completely stealth.Since it involves passive fingerprinting.
Technical information :- It helps the attacker in collecting data or information, which might help the attacker in locating and exploring the vulnerabilities in the technical infrastructure of the target host.
Secondary data :- Apart from the technical data,a lot of non-technical data.
TYPES OF FOOTPRINTING
Open source footprinting
It’s the safest type of footprinting as it is within legal limits,and one can do it without any fear of doing any kind of illegal activity.
It includes finding basic information like : locating phone numbers,e-mail addresses,performing whois query for the domain name, searching through DNS tables and scanning certain IP addresses through automated tools.
Network Enumeration
This is a computing activity in which user names and information on groups,shares and services of networked computers. It only retrives information about which servers are connected to a specifi network,and what operating system is run on them. They also searches for the registrar information.
If you have any concerns or any difficulties on this guide then feel free to place a reply on this thread to get instant help.
Top 10 Best Android Hacking Apps - 2017-18, for Rooted Devices
1) Wifi Kill
WiFi Kill is one of the best apps for disabling other user wifi connection from your android mobile. You just need to download this amazing android app on your phone and you can easily kick off another user from connected wifi . Make sure your phone is rooted and if not follow our guide for rooting android phone.
Features of WiFi Kill Apk
-You can see the list of devices in the wifi network that you are using.
-WifiKill can show the data transfer rate (download, upload) of grabbed devices.
-You can monitor the network activity of any device using wifi.
Names of the devices connected to the network are displayed.
-Most importantly, you can cut off the net connection of any device which is connected to the same wifi network as yours.
-It works on tablets too.
Here is the download link--->
http://www.mediafire.com/download/wycg4qyx4168euz/WiFiKill.apk
2) Zanti
ZAnti Penetration Testing Android Hacking Toolkit
This is one of the favourite tools for hacking networks and run security tests on wifi networks. You can find almost all security tools related to hacking any wifi networks from this android app. ZAnti is one of the most impressive android app related to hacking from android phone.
Take a look at things you can do with zANTI:-
-Change device's MAC address.
-Create a malicious WiFi hotspot.
-Hijack HTTP sessions.
-Capture downloads.
-Modify HTTP requests and responses.
-Exploit routers.
-Audit passwords.
-Check a device for shellshock and SSL poodle vulnerability.
Here is the download link--->
http://www.mediafire.com/download/1v84ktmoohlhy8o/zANTI.apk
3) Hackode
The hacker's Toolbox is an application for penetration tester, Ethical hackers, IT administrator and Cyber security professional to perform different tasks like reconnaissance, scanning performing exploits etc.
This Application contains different tools like:-
DNS lookup
IP
MX Records
DNS Dig
Exploits
Security Rss Feed
Google Hacking
Google Dorks
Whois
Scanning
Ping
Trace route
Here is the download link--->
http://www.mediafire.com/download/z30p75abmtkl4bn/Hackode_v1.1_apkpure.com.apk
4) Wps Wpa Tester
If you really want to hack wifi password from android mobile download WPS connect wifi password hacking android app. You can easily connect any wifi network without password from this wifi hacking apk. But make sure that wifi runs on wps security. This android app has a collection of master key routers that runs in wps security mode. So you can easily hack any wps networks and bypass security and connect your android mobile device with wifi.
Here is the download link--->
http://www.mediafire.com/download/qvb9p5ee5ztgn3t/Wps+Wpa+Tester+Premium+v2.7.5.iHackedit.com.apk
5) Dsploit
DSploit is an Android network analysis and penetration suite which aims to offer to IT security experts/geeks the most complete and advanced professional toolkit to perform network security assessments on a mobile device.
Here is the download link--->
http://www.mediafire.com/download/mlo4aqh0hf2ruj7/DSploit.apk
6) SSl STRIP
In SSL Strip, all the traffic from the victim’s machine is routed via a proxy that is created by the attacker. It can be thought of as a Man-In-the-Middle attack (MITM).
A lot of documentation seems to indicate that it simply replaces occurrences of "https" with "http" in traffic that it has access to. So a URL passing through such as "https://facebook.com" would be passed on the to victim as "http://facebook.com".
Here is the download link--->
http://www.mediafire.com/download/jpbxpiusqp59cql/SSLStrip+for+Android+Root_v1.0_apkpure.com.apk
7) AndroDumper
Your WiFi network is your conveniently wireless gateway to the internet and you will secure your network with a password.
You probably secure your network using the more bulletproof WPA security protocol 'cause you know how easy it is to crack a WEP password.
But, a new, free, open-source tool called AndroDumpper can crack most routers' current password.
You can download it from the link given below. The Application will try to connect to WPS enabled WiFi Routers that have the WPS vulnerability uisng some algorithms to connect to the WiFi.
A nearby WPA-secured WiFi network. Technically, it will need to be a network using WPA security with the WPS feature enabled.
Here is the download link--->
http://www.mediafire.com/download/96xkgcqgv9ikfa5/AndroDumpper+WPS+Connect_v1.86_apkpure.com.apk
8) Penetrate Pro
Android app allows you to decode and access a secure WiFi Network from Android.Android devices are popular among penetration testers and it’s very easy to use penetration testing on an Android.
Penetrate Pro is a great, handy app for getting access to the secure WiFi network from Android smartphones and tablets. The app calculates WEP/WPA keys for some WiFi routers and lets you get access by using the password. Unlock WiFi with Penetrate Pro android app.
Note that some antivirus apps think it’s a virus because it is a security-related tool. Don’t be concerned, Penetrate pro won’t affect the regular function of your phone.
Here is the download link--->
http://www.mediafire.com/download/p3tpcpnf1tdv6rt/Penetrate+Pro.apk
9) Wifi Inspect
WiFi inspects android app scan your wifi networks for vulnerability. You can see other user IP address from this android app. Basically, this android app scans other IP address, mac address and device name.
Here is the download link--->
http://www.mediafire.com/download/w9zf3p8g1v5wyaq/WiFinspect.apk
10) Nmap
Nmap is a popular network security scanner which is also available for android devices. It is used by professionals for network exploration. It works on both non-rooted and rooted phones, But if your device is rooted then you have access to some more features.
Here is the download link--->
http://www.mediafire.com/download/8p34wdg6rhy8q3q/anmap.apk
Windows User Account Hacking
Windows user Account can be Hacked by using Command Prompt.This type of Hacking is done in order to gain illegal access to the user account and steal the data in the system.
Note:This type of Hacking can be done only on User Accounts which have Administrative rights.
Note:This type of Hacking can be done only on User Accounts which have Administrative rights.
Commands Used For User Account Hacking
1.To See all the account present on the Computer.
Net user
2.To change the password of a User account without knowing the old password.
Net user administrator *
3.To make a new user account.
Net user hacker /add
4.To Delete the existing user account.
Net user hacker /delete
5.To make a hidden account in the computer.{Works only with Windows XP}
Net User hacker /add
Net localgroups users hacker /delete
Note:-
To login to this hidden account press
Ctrl+Alt+Delete+Delete
And give the hidden user name in the user name field and password in password field respectively.
The term hacker refers the user name or name of the account.
Counter Measures of Windows User Account Attack
1.Change the Boot sequence in the BIOS setup.Keep Hard Disk as 1st boot drive, then CD\DVD drive as 2nd boot device and Removable port as 3rd boot device.
2.Put the BIOS password.
3.Put the physical lock behind the cabinet of PC. (Put Lock).
Windows Hack using Remote Desktop Connection

Remote Desktop is a feature of Windows Server 2003 that lets you remotely log on to and work at a machine as if you were seated at the local console (in Windows 2000 Advanced Server, this feature was called Terminal Services in Remote Administration Mode). Remote Desktop can be a lifesaver for fixing problems on servers at remote sites. Below is a step by step guide for Windows Hack using Remote Desktop Connection
Step 1: Enable RDP Server on a One System
Next, click on the “Allow Remote Assistance connections to this computer” and click “Apply.”
Cain and Abel, besides being a great password cracking tool (albeit a bit slow) is probably the best MiTM tool on the market—and it is free!
Step 3: Use ARP Scan on Systems with Cain
Click on the Sniffer button on Cain, then select the Sniffer tab, then select theHosts tab at the bottom, then click on the blue + on the top menu, select theRadio button, select the target IP range, and click OK.
Here, we see the hosts on the network.
Below, we are connecting to the RDP server called Null Byte.
Cain and Abel is now capturing the entire session and saving it into a file named in the far right column. We can now right click on that filename and choose View to open the decrypted file in Notepad.
Step 8: Search for Traffic
Now that all the traffic on the RDP connect is traveling through our attack system, we can search for traffic of interest to us.
Ideally, we want the sysadmin password for RDP. If we can find the sysadmin password for RDP, we will likely be able to use RDP on any of the network’s machines as usually the sysadmin will set up RDP with the same password on every system for convenience.
Even better, many sysadmin use the same password to remote into client machines as they use on their system and other accounts. This means that when we capture this password we may own the entire domain and network!
To find any keys pressed in the hexadecimal file capture, use the Find feature in Notepad to search for “key pressed”. This will find each of the keystrokes, one-by-one, of any keystrokes entered by the sysadmin including their password.
Hope you like this article of Windows Hack using Remote Desktop Connection.
Hack Into A Computer Which Is Connect On same network (Lan)
If you are working in Office / Colleges and want to hack your friends & college mate PC then here is a trick.
What do we need ?
- Windows Os
- Cain And Abel
Step 1:- Finding the target
So first off we need to find a computer or the computer to hack into. So if your
plugged in to the LAN, or connected to the WAN, you can begin. Open up Cain and
Abel. This program has a built in sniffer feature. A sniffer looks for all IP addresses in the local sub net. Once you have opened up the program click on the sniffer tab, click the Start/Stop sniffer, and then click the blue cross.
plugged in to the LAN, or connected to the WAN, you can begin. Open up Cain and
Abel. This program has a built in sniffer feature. A sniffer looks for all IP addresses in the local sub net. Once you have opened up the program click on the sniffer tab, click the Start/Stop sniffer, and then click the blue cross.
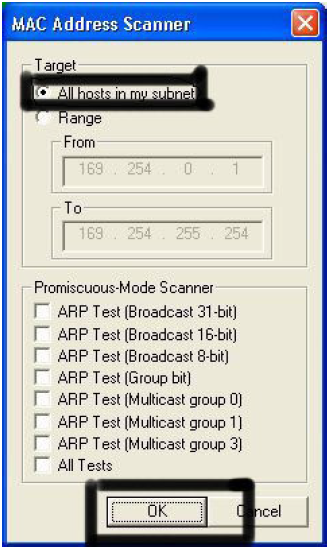
Another window will pop up, make sure “All host in my subnet” is selected, and then
click ok.
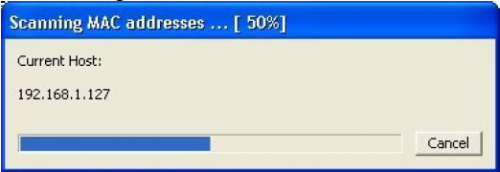
It should begin to scan.
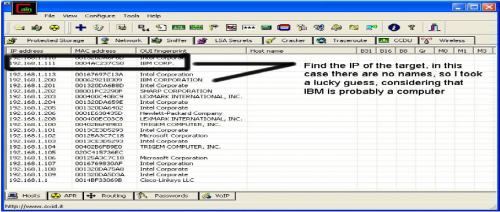
Then IP’s, computer names, and mac addresses will show up
Now remember the IP address of the computer you are going to be breaking into.
If you can’t tell whether the IP address is a computer, router, modem, etc, that’s ok.
During the next step we will begin our trial and error.
During the next step we will begin our trial and error.
Step 2:- Trial and error
Now, we don’t know if we have our designated target, or if we have a computer or
printer, or whatever else is on the LAN or WAN.
If you did get the IP of the target though, I still recommend reading through this
section, for it could be helpful later on.
Click on the start menu and go to run, type in cmd, and click ok.
This should bring up the command prompt.
From here we will do most of the hacking.
Now I will be referring to certain commands that need to be inputted into the
command prompt.
I will put these commands in quotes, but do not put the quotes in the code when you
type it into the prompt.
I am only doing this to avoid confusion.
Let’s get back to the hacking.
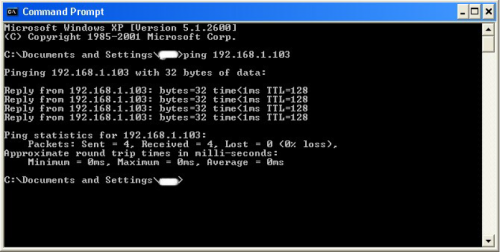
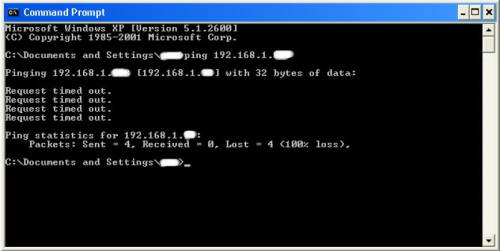
Type in “ping (IP address of the target).” For example in this tutorial, “ping
192.168.1.103.”
This will tell us if the target is online.
If it worked, it will look something like this (note, I have colored out private
information):
printer, or whatever else is on the LAN or WAN.
If you did get the IP of the target though, I still recommend reading through this
section, for it could be helpful later on.
Click on the start menu and go to run, type in cmd, and click ok.
This should bring up the command prompt.
From here we will do most of the hacking.
Now I will be referring to certain commands that need to be inputted into the
command prompt.
I will put these commands in quotes, but do not put the quotes in the code when you
type it into the prompt.
I am only doing this to avoid confusion.
Let’s get back to the hacking.
Type in “ping (IP address of the target).” For example in this tutorial, “ping
192.168.1.103.”
This will tell us if the target is online.
If it worked, it will look something like this (note, I have colored out private
information):
IF it didn’t work, meaning that the target is not online, it will look something like this:
If the target is not online, either switch to a different target, or try another time.
If the target is online, then we can proceed.
If the target is online, then we can proceed.
Step 4:– Gathering the information
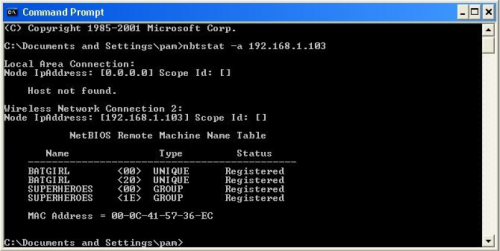
Now, input this command “nbtstat –a (IP address of target).” An example would be
“nbtstat –a 192.168.1.103.”
This will show us if there is file sharing enabled, and if there is, it will give us the:
currently logged on user, workgroup, and computer name.
“nbtstat –a 192.168.1.103.”
This will show us if there is file sharing enabled, and if there is, it will give us the:
currently logged on user, workgroup, and computer name.
Step 5:- Getting In
Finally it’s time.
By now we know: that our target is online, our target has file sharing, and our target’s
computer name.
So it’s time to break in.
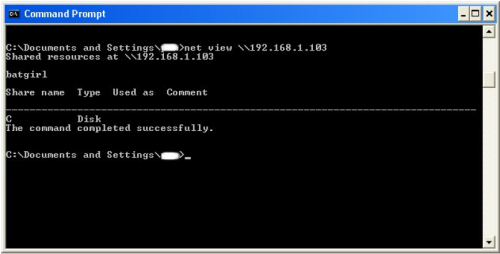
We will now locate the shared drives, folders, files, or printers. Type in “net view
(IP Address of Target)”
An example for this tutorial would be: “net view 192.168.1.103”
By now we know: that our target is online, our target has file sharing, and our target’s
computer name.
So it’s time to break in.
We will now locate the shared drives, folders, files, or printers. Type in “net view
(IP Address of Target)”
An example for this tutorial would be: “net view 192.168.1.103”
We have our just found our share name. In this case, under the share name is “C,”
meaning that the only shared thing on the computer is C. Then to the right, under
Type, it says “Disk.” This means that it is the actual C DISK of the computer. The C
DISK can sometimes be an entire person’s hard drive.
Type, it says “Disk.” This means that it is the actual C DISK of the computer. The C
DISK can sometimes be an entire person’s hard drive.
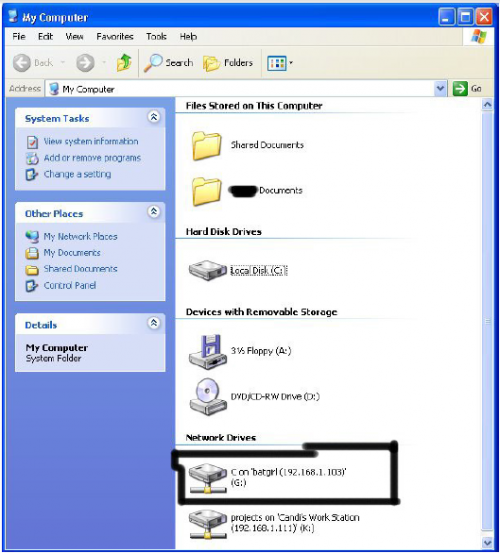
As you can see, for my hack I have already used “K,” so I used “G” instead.
You may also do the same for multiple hacks.
If it worked, it will say “The command completed successfully.”
If not, you will have to go retrace you steps.
Now open up “my computer” under the start menu, and your newly created network
drive should be there.
If it worked, it will say “The command completed successfully.”
If not, you will have to go retrace you steps.
Now open up “my computer” under the start menu, and your newly created network
drive should be there.
Now, if you disconnect from the WAN or LAN, you will not be able to access this
drive, hence the name Network Drive.
The drive will not be deleted after you disconnect though, but you won’t be able to
access it until you reconnect to the network.
So if you are doing this for the content of the drive, I recommend dragging the files
and folders inside of the drive onto your computer,
because you never know if the target changes the sharing setting.
Congratulations! You’re DONE!
-Commands used in this tutorial:
PING
NBTSTAT -a (IP Address of Target)
NET VIEW (IP Address of Target)
NET USE K: (IP Address of Target)(SHARENAME)
-Program used in this tutorial:
Cain and Abel.
PING
NBTSTAT -a (IP Address of Target)
NET VIEW (IP Address of Target)
NET USE K: (IP Address of Target)(SHARENAME)
-Program used in this tutorial:
Cain and Abel.

















Nice Post...
ReplyDeleteI'm having very interesting information regarding Hire Professional Hackers!